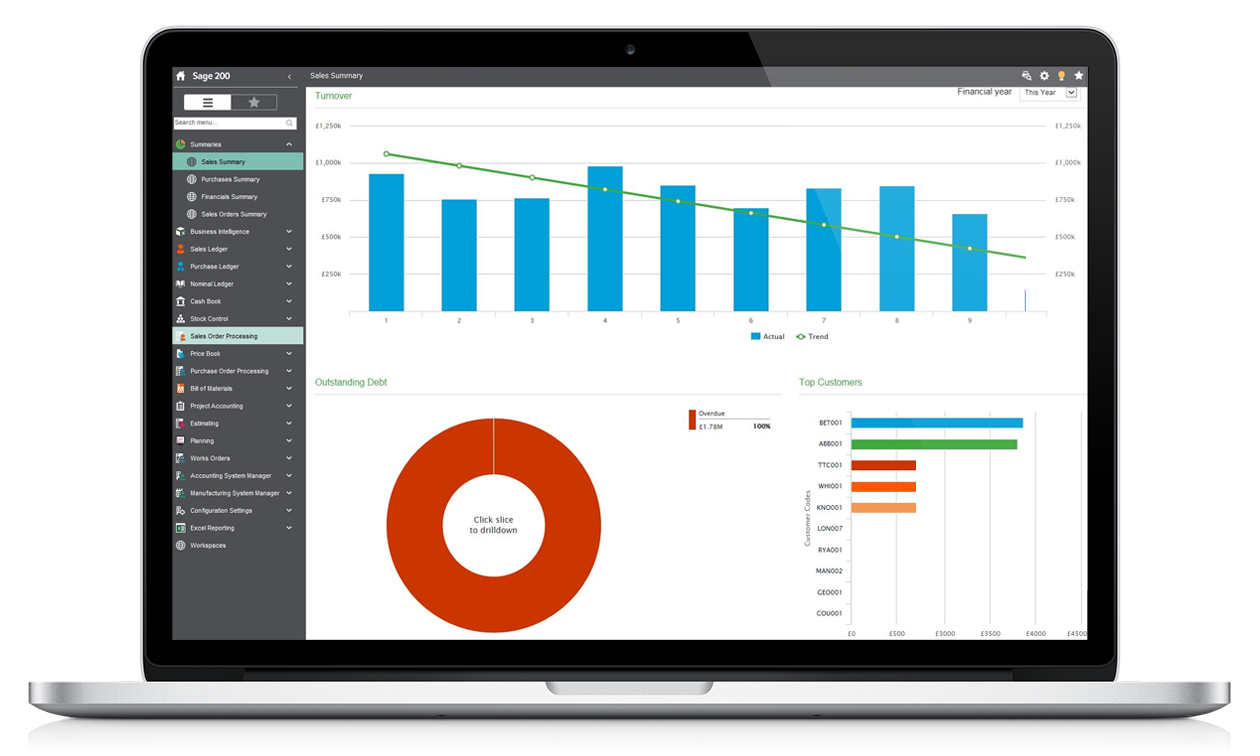
Protronics provide help and expertise for Sage software, particularly Sage 50 and Sage 200. Sage projects can be fast moving, innovative, even transforming; sometimes they even make the previously impossible possible. We do all of that (we have smart, committed people and bags of experience helping organisations change), but at heart we aim to be dependably dull. More..
We offer fast and expert Sage 50 support and Sage 200 support. We have offices in London, Yorkshire and Oxford, but support Sage users nationwide.
Demanding Sage 50 user? Expertise to help you stretch it, clear advice if you need to move on from it
Learn MoreCareful, calm and competent migration and upgrades to Sage 200. Candid advice if you shouldn't upgrade yet.
Learn MoreGood Sage support is necessary, but isn't always sufficient. For when you need involvement, foresight and solutions.
Learn MoreIntegration with web shops, outsourced warehouses, and many others. Experience, pragmatism and answers available.
Learn MoreWe solve technical and business problems involving and using Sage accounts software and are:
Committed, always seeing problems and projects through.
Experienced (our Sage staff have over 10 year’s experience on average).
Smart enough for when it’s needed (that’s all of us, not just the two software developers with doctorates!).
Grounded in accounting principles and accounts processes, as well as Sage experts.
Pragmatic and look for simple solutions first, while not being afraid when complex solutions are needed.
Notable for attention to detail, committed to solid foundations, and in all the good ways dependably dull.
